Role of VPN in Remote Work Security and Compliance

More than 60 percent of American mid-sized enterprises now manage hybrid teams that rely on remote connectivity every day. As digital threats evolve, ensuring secure access to company systems has become a top priority for IT managers in cities like Philadelphia and Baltimore. This article explains how Virtual Private Networks help protect sensitive business data and maintain reliable connections, enabling distributed teams to work securely in complex environments.
Table of Contents
- What Is A VPN And Its Role In Remote Work
- Types Of VPN Solutions For Distributed Teams
- How VPNs Enhance Data Security And Access
- VPNs And Regulatory Compliance In The U.S.
- Risks, Limitations, And Cost Implications
- Choosing And Managing VPNs For Enterprise Use
Key Takeaways
| Point | Details |
|---|---|
| VPN Importance | VPNs are essential for secure remote work, providing encrypted access to corporate networks and protecting sensitive data during transmission. |
| Types of VPN Solutions | Key VPN types include Remote Access VPNs for individual connectivity, Site-to-Site VPNs for multiple locations, and Extranet VPNs for external partner collaboration. |
| Data Security Enhancements | VPNs enhance data security by encrypting traffic, masking IP addresses, and enabling secure access controls. |
| Compliance Considerations | Organizations must ensure their VPN solutions meet industry-specific regulatory requirements to protect sensitive information and maintain compliance. |
What Is a VPN and Its Role in Remote Work
A Virtual Private Network (VPN) is a secure digital pathway that allows remote workers to access corporate networks safely over the internet. By creating an encrypted connection, VPNs transform public networks into private, protected communication channels for distributed teams. This technology has become essential in modern workplace environments where employees frequently work from diverse locations.
The core function of a VPN is to establish a secure communication tunnel over public networks, ensuring that sensitive corporate data remains confidential during transmission. When an employee connects through a VPN, their internet traffic gets encrypted, preventing unauthorized access and protecting critical business information from potential cybersecurity threats. This encryption process happens instantaneously, creating a secure bridge between remote workers and their organization’s internal systems.
VPNs serve multiple critical functions in remote work security landscapes:
- Encrypt network communications
- Mask user IP addresses
- Provide secure access to corporate resources
- Protect against potential cyber intrusions
- Enable compliance with data privacy regulations
Pro tip: Configure your VPN with multifactor authentication to add an extra layer of security beyond standard password protection.
Types of VPN Solutions for Distributed Teams
Distributed teams require diverse VPN solutions tailored to specific organizational needs and network architectures. Different types of VPN technologies offer unique approaches to securing remote workforce communications, each designed to address specific connectivity and security challenges encountered in modern workplace environments.
The primary VPN categories for distributed teams include:
- Remote Access VPNs: Enable individual employees to securely connect to corporate networks from any location
- Site-to-Site VPNs: Connect multiple office locations through encrypted network tunnels
- Extranet VPNs: Facilitate secure communication between an organization and external partners
When selecting VPN solutions, organizations should prioritize standards-based Internet Key Exchange/Internet Protocol Security (IKE/IPsec) protocols. These validated protocols provide robust security mechanisms that protect against potential network intrusions and ensure data confidentiality. Enterprise-grade VPN solutions typically incorporate advanced features like multi-factor authentication, split tunneling, and comprehensive logging capabilities to enhance overall network security.
The table below highlights the main types of VPN solutions for distributed teams and their ideal use cases:
| VPN Type | Best For | Typical Deployment |
|---|---|---|
| Remote Access VPN | Individual employees working offsite | Laptop and mobile device connections |
| Site-to-Site VPN | Multiple office locations | Permanent inter-branch links |
| Extranet VPN | Collaboration with partners | Secure partner company access |
Pro tip: Conduct periodic security audits of your VPN infrastructure to identify and address potential vulnerabilities before they can be exploited.
How VPNs Enhance Data Security and Access
Virtual Private Networks (VPNs) play a critical role in securing remote workforce communications by creating robust protection mechanisms for sensitive organizational data. VPNs establish encrypted communication tunnels that safeguard information transmitted across potentially vulnerable public networks, effectively shielding corporate resources from unauthorized access and potential cyber threats.
The primary data security enhancements provided by VPNs include:
- Encryption of network traffic: Transforms data into unreadable code during transmission
- IP address masking: Conceals user’s actual geographic location
- Secure access control: Restricts network resource access to authenticated users
- Network segmentation: Prevents unauthorized lateral movement within corporate networks
Enterprises can significantly strengthen their remote work security by implementing multi-factor authentication and maintaining rigorous VPN configuration standards. Modern VPN solutions incorporate advanced security features like comprehensive logging, real-time threat monitoring, and adaptive authentication protocols that dynamically assess user risk profiles. These technological safeguards ensure that distributed teams can securely access critical organizational resources without compromising sensitive data integrity.

Pro tip: Regularly update VPN client software and conduct periodic security assessments to maintain optimal protection against emerging cyber vulnerabilities.
VPNs and Regulatory Compliance in the U.S.
Regulatory compliance represents a critical consideration for organizations implementing remote work technologies, with Virtual Private Networks (VPNs) serving as a key mechanism for meeting stringent federal security requirements. Federal guidance from national security agencies emphasizes selecting standards-based VPN solutions that meet rigorous protection protocols, particularly for sectors handling sensitive government and industrial data.
Different industries face unique compliance challenges when implementing VPN technologies:
- Healthcare: Must adhere to HIPAA data protection standards
- Defense Contractors: Required to follow Department of Defense cybersecurity frameworks
- Financial Services: Obligated to meet SEC and GLBA security regulations
- Government Agencies: Bound by strict FISMA and NIST security guidelines
Specific regulatory requirements demand that VPN solutions implement robust authentication mechanisms and comprehensive data protection strategies, ensuring that remote access does not compromise organizational data integrity. Enterprise VPN configurations must incorporate multi-factor authentication, advanced encryption protocols, and continuous monitoring capabilities to maintain compliance across various regulatory landscapes. This approach helps organizations systematically address potential security vulnerabilities while enabling secure, flexible remote work environments.
Here is a summary of major industry-specific regulatory standards affecting VPN use in the U.S.:
| Industry | Key Regulation | Compliance Focus |
|---|---|---|
| Healthcare | HIPAA | Patient data privacy and security |
| Financial Services | GLBA, SEC rules | Customer information protection |
| Defense Contractors | DoD standards | Defense data access control |
| Government Agencies | FISMA, NIST | Federal system integrity |
Pro tip: Consult with your industry’s specific regulatory compliance experts to develop a tailored VPN implementation strategy that meets all required security standards.
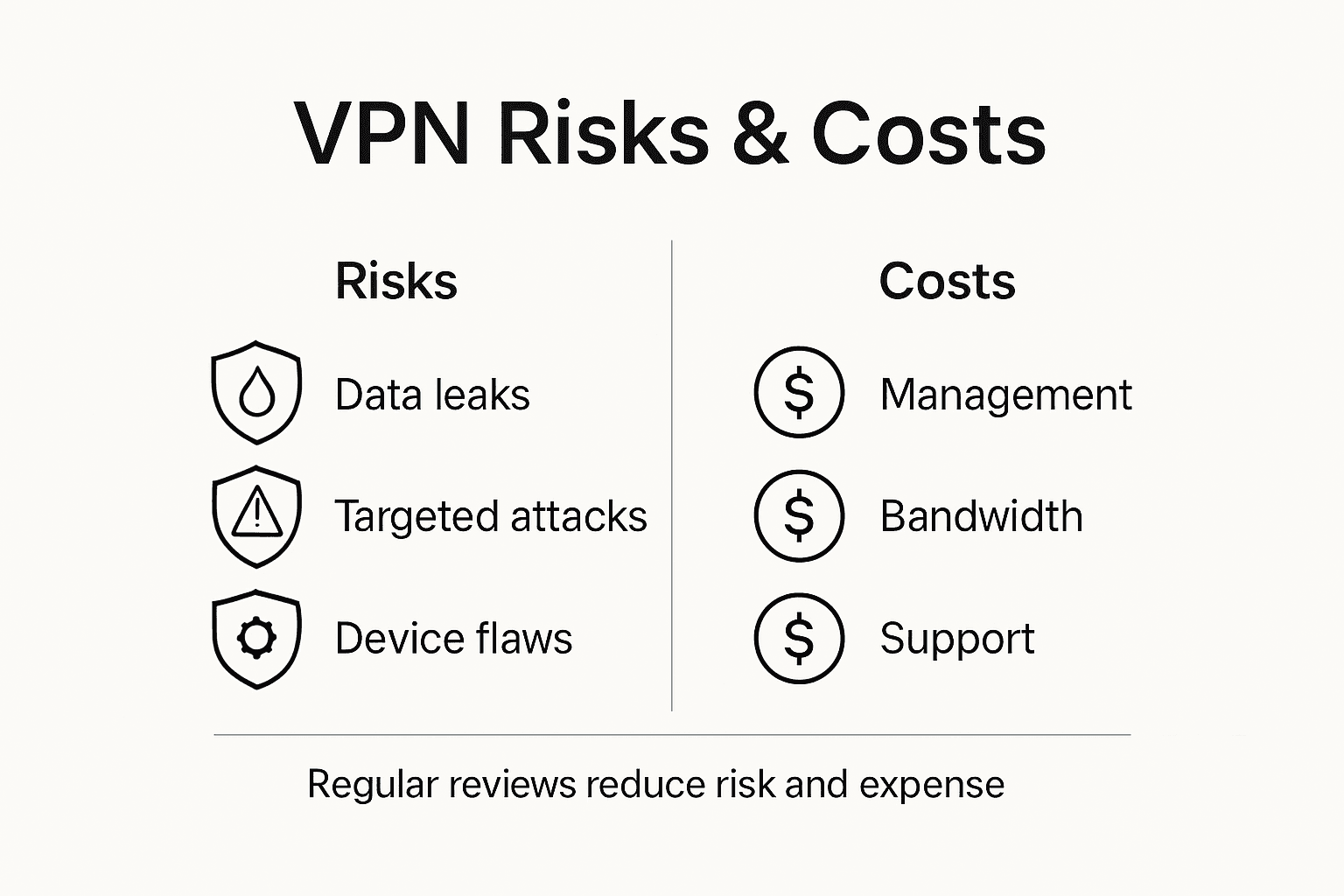
Risks, Limitations, and Cost Implications
VPN technologies, while crucial for secure remote work, come with complex operational challenges that organizations must carefully navigate. National security agencies have identified significant risks associated with VPN deployments, including potential exploitation by sophisticated threat actors, which can compromise entire network infrastructures.
Key risks and limitations for enterprise VPN implementations include:
- Vulnerability Exposure: VPN devices can become primary targets for cyberattacks
- Performance Bottlenecks: Potential bandwidth restrictions and connection speed degradation
- Complex Management: Continuous infrastructure maintenance and security updates required
- Authentication Challenges: Increased complexity in managing user access and identity verification
Advanced security analytics platforms can help organizations mitigate VPN-related risks by identifying suspicious traffic patterns and potential network intrusions. Cost implications extend beyond simple licensing fees, encompassing infrastructure investments, ongoing security monitoring, staff training, and potential productivity losses during system configurations. Enterprise leaders must conduct comprehensive cost benefit analyses that factor in direct expenses and potential cybersecurity risks when implementing VPN solutions.
Pro tip: Conduct quarterly comprehensive security assessments of your VPN infrastructure to proactively identify and address potential vulnerabilities before they can be exploited.
Choosing and Managing VPNs for Enterprise Use
Selecting the appropriate Virtual Private Network (VPN) for enterprise environments requires a strategic approach that balances security, performance, and operational flexibility. National security agencies recommend implementing standardized VPN solutions that have been validated under rigorous cybersecurity frameworks, ensuring robust protection against potential network vulnerabilities.
Critical considerations for enterprise VPN selection include:
- Authentication Mechanisms: Multi-factor authentication capabilities
- Protocol Standards: Support for validated IKE/IPsec protocols
- Scalability: Ability to support distributed workforce requirements
- Monitoring Capabilities: Comprehensive logging and threat detection features
- Performance: Minimal latency and bandwidth restrictions
Cybersecurity experts emphasize the importance of continuous VPN management, including regular patch updates, capacity testing, and strategic user access controls. Enterprise VPN strategies must incorporate dynamic risk management approaches that adapt to evolving technological landscapes. This involves implementing rate limiting strategies, prioritizing essential user access during peak demand, and maintaining a proactive security posture that anticipates potential network intrusion attempts.
Pro tip: Develop a comprehensive VPN governance framework that includes quarterly security assessments, continuous employee training, and automated threat monitoring systems.
Secure Your Remote Workforce with SabertoothPro Solutions
As this article highlights, the role of VPNs in protecting remote work environments is more critical than ever. Businesses face significant challenges securing sensitive data, managing user access, and ensuring compliance with industry regulations. If you are looking to strengthen your organization’s remote connectivity while safeguarding your digital infrastructure, exploring advanced solutions can make all the difference. SabertoothPro specializes in delivering high-speed, secure, and reliable internet options designed to support VPNs and other security technologies effortlessly.
Empower your distributed teams with robust network security and seamless connectivity by integrating SabertoothPro’s offerings tailored for modern enterprises. From next-gen security frameworks to scalable IoT and cloud integrations, we help you address encryption, access control, and performance challenges head on. Don’t compromise when it comes to securing your remote workforce. Discover our Wifi Extenders to boost network strength and visit SabertoothPro.com for cutting-edge internet and enterprise IT solutions that build resilience and compliance into your digital operations today.
Frequently Asked Questions
What is a VPN and how does it enhance remote work security?
A VPN, or Virtual Private Network, creates a secure encrypted connection over the internet, allowing remote workers to access corporate networks safely. It protects sensitive data during transmission and ensures that communications are kept confidential from unauthorized access.
What types of VPN solutions are available for remote work?
The main types of VPN solutions include Remote Access VPNs for individual employees, Site-to-Site VPNs for connecting multiple office locations, and Extranet VPNs for secure collaboration with external partners.
How can organizations ensure compliance with data regulations while using a VPN?
Organizations can ensure compliance by selecting VPN solutions that implement robust authentication mechanisms, advanced encryption protocols, and continuous monitoring capabilities, addressing specific regulatory standards such as HIPAA or GLBA relevant to their industry.
What are the key risks associated with VPN implementation in remote work environments?
Key risks include vulnerability exposure where VPN devices may become targets for cyberattacks, performance bottlenecks affecting connection speed, complex management requirements, and challenges in managing user access and identity verification.


