Why Secure Connectivity Matters for CIOs Today

Protecting sensitive data in busy healthcare clinics or retail chains across cities like Baltimore, Philadelphia, and Richmond is never just about plugging in a new device. Every day, patient records and payment details travel across networks that can open the door to risk if security is only skin deep. Many leaders believe their antivirus or a firewall alone will keep threats at bay, but true security demands layered protection and continuous visibility. This article breaks down what secure connectivity means for your organization and exposes common myths that put your business at risk.
Table of Contents
- Defining Secure Connectivity And Common Myths
- Types Of Secure Connectivity Solutions
- Connectivity Infrastructure Considerations
- How Secure Connectivity Supports Daily Operations
- Regulatory Impact For Healthcare And Retail
- The Business Case Beyond Compliance
- Risks Of Poor Connectivity And Mitigation Strategies
- Mitigation Strategies That Actually Work
- Comparisons With Traditional, Less-Secure Networks
- How Modern Secure Connectivity Differs
Key Takeaways
| Point | Details |
|---|---|
| Understanding Secure Connectivity is Essential | Secure connectivity involves multiple layers of protection including encryption, authentication, and monitoring to safeguard data transmitted across networks. |
| Correct Assumptions are Crucial | Organizations must challenge common myths regarding cybersecurity, as relying solely on firewalls or antivirus software can create vulnerabilities. |
| Compliance is Mandatory | Regulations like HIPAA and PCI DSS enforce strict security measures; violations can result in severe penalties. |
| Collaboration Improves Security | Integrating security planning with operational technology from the outset enhances the overall security posture and helps prevent gaps. |
Defining Secure Connectivity and Common Myths
Secure connectivity sounds straightforward until you start digging into what it actually means for your organization. At its core, secure connectivity refers to network communications protected through encryption, authentication, and continuous monitoring to prevent unauthorized access and data breaches. For CIOs managing healthcare systems or retail operations in the Mid-Atlantic region, this is not an abstract concept. Your patient records, payment card data, and employee credentials move across your networks every single day. Without proper security controls, every transmission becomes a potential vulnerability.
Here’s where most CIOs run into trouble: they inherit a patchwork of connectivity solutions and assume that because traffic travels through what looks like a “secure” connection, their data is actually protected. That assumption creates blind spots. Secure connectivity requires multiple layers working together. You need encrypted tunnels for data in transit, strong authentication protocols to verify who is accessing your network, real-time visibility into traffic patterns, and the ability to isolate compromised devices before they spread infection. Many organizations focus only on the encryption piece and miss the other critical components. Common cybersecurity myths reveal that organizations often underestimate threats to smaller networks or believe antivirus software alone provides sufficient protection, when in reality layered security approaches are essential.
Let’s address some widespread myths that damage security strategies:
- “Small networks don’t attract attackers.” Healthcare clinics and mid-sized retail chains with 50 to 500 employees are actually prime targets. Your smaller IT teams mean fewer people monitoring threats, and your valuable patient or customer data makes you worth attacking.
- “A firewall handles all connectivity security.” Firewalls inspect traffic at your network edge, but they cannot see inside encrypted data, authenticate individual users, or detect when an authorized user is doing something malicious.
- “We secured our network once, so we’re protected.” Security is not a destination. New vulnerabilities emerge constantly. Ransomware groups evolve their tactics monthly. Your connectivity posture from last year provides almost no protection against today’s threats.
- “Cloud connectivity means your provider handles security.” Your cloud provider secures their infrastructure, but you remain responsible for controlling who accesses your data and how it moves between systems.
- “Expensive security tools guarantee safety.” Spending six figures on a security platform without configuring it properly or having people to manage it provides false confidence and false protection.
What separates organizations with strong connectivity security from those experiencing breaches is clarity about what they’re protecting and a willingness to challenge assumptions. You need to know every path your sensitive data takes. You need to understand which devices connect to your network and why. You need visibility into what’s crossing network boundaries at this exact moment, not just historical logs from yesterday.
For healthcare organizations storing Electronic Health Records, regulatory frameworks like HIPAA demand specific security controls around connectivity. For retail operations processing credit cards, PCI DSS compliance requires encryption and network segmentation. These aren’t suggestions. They’re legal obligations tied to significant penalties if violated. The connectivity infrastructure that supports these systems must be engineered specifically for compliance, not built as an afterthought.
Pro tip: Conduct an honest audit of your current connectivity by asking three questions: Can we see all devices connecting to our network? Can we trace the path of sensitive data from creation to storage? Can we identify within minutes if unauthorized access occurred? If you cannot answer yes to all three, your secure connectivity strategy has critical gaps.
Types of Secure Connectivity Solutions
Not all secure connectivity solutions work the same way, and what works for a retail headquarters downtown won’t necessarily protect a clinic with multiple satellite locations across three states. Your choice of connectivity infrastructure directly shapes your security posture, your compliance readiness, and ultimately your ability to respond when threats emerge. Understanding the main categories of secure connectivity solutions helps you build a defense strategy tailored to your organization’s actual structure and vulnerabilities.
Virtual Private Networks (VPNs) create encrypted tunnels between your devices and your network infrastructure, making data unreadable to anyone intercepting traffic. For healthcare organizations with remote staff accessing Electronic Health Records or retail managers checking inventory from home, VPNs have become baseline security. However, VPNs alone have limits. They authenticate users at connection time but don’t continuously verify that connected devices remain trustworthy. A VPN can give a compromised laptop full access to your network just because it authenticated yesterday. This is why VPN usage in remote work has evolved beyond simple tunnel protection.
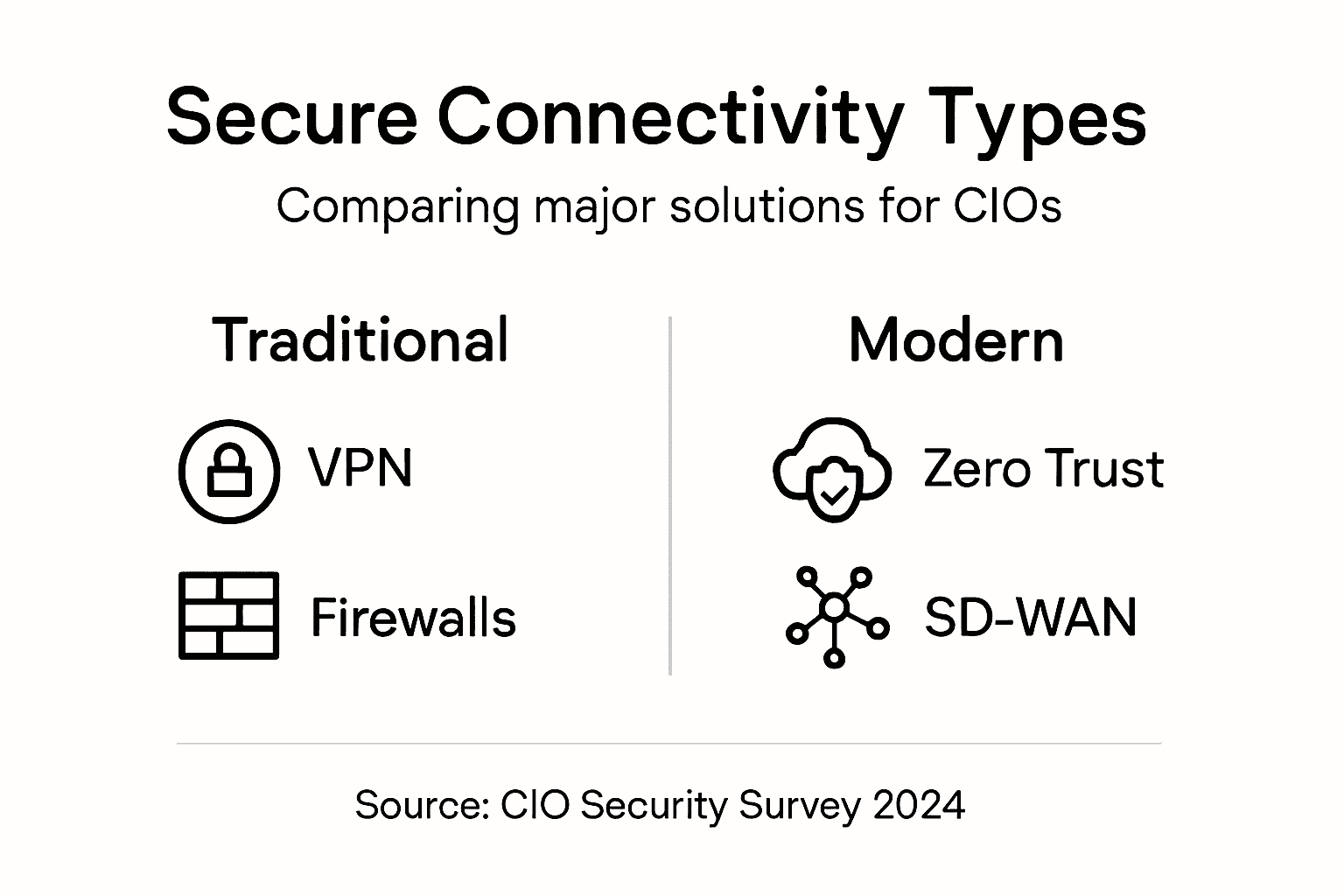
Zero-Trust Architecture flips the security model. Instead of trusting anything inside your network, zero-trust assumes all connections are potentially hostile until proven otherwise. Every device gets verified. Every user gets authenticated. Every access request gets evaluated against specific policies. For a retail operation managing point-of-sale systems, inventory networks, and customer Wi-Fi, zero-trust means a compromised register cannot automatically access your backend inventory system just because it is on your network. Zero-trust requires more infrastructure investment and ongoing management, but it catches threats that traditional perimeter-based security misses.
Software-Defined WAN (SD-WAN) and Secure Access Service Edge (SASE) solutions consolidate connectivity and security into a single platform. Rather than routing all traffic through a central firewall thousands of miles away, these solutions apply security policies at the network edge, closer to where data originates. For healthcare systems with multiple clinic locations, this means patient data gets inspected and secured locally rather than being backhaul to a central facility. SASE specifically integrates firewall, threat prevention, and secure web gateway functions into one cloud-based service, eliminating the false choice between connectivity speed and security strength.
Network segmentation divides your infrastructure into separate zones with restricted access between them. Your patient records live in one segment with strict controls. Your guest Wi-Fi exists in another with no access to clinical systems. Your secure connectivity principles for operational technology emphasize limiting exposure through this kind of segmentation. A retail operation might segment credit card processing systems completely separately from customer-facing Wi-Fi, ensuring that if guest networks get compromised, attackers cannot reach payment systems.
Next-Generation Firewalls (NGFW) inspect not just what data is moving, but what application generated it and whether that application should be sending that data. A legacy firewall sees encrypted video traffic and allows it through. An NGFW can identify that the traffic comes from an unauthorized streaming application and block it, even though it cannot see inside the encryption. For healthcare and retail environments handling sensitive data, NGFWs provide visibility into application-level threats that traditional firewalls miss.
Here’s a comparison of leading secure connectivity solutions for healthcare and retail:
| Solution Type | Primary Strength | Typical Weakness | Best Use Case |
|---|---|---|---|
| VPN | Simple remote access, strong in-transit encryption | Does not verify device trust continuously | Remote staff needing to access sensitive records |
| Zero-Trust Architecture | Continuous verification, granular policies | Higher implementation complexity and cost | Organizations with diverse, high-value assets |
| SD-WAN/SASE | Consolidated security at network edge | Initial investment and configuration | Multi-site clinics or retail chains |
| Network Segmentation | Limits lateral movement of threats | Can be complex to manage over time | Isolating payment or patient data environments |
| Next-Gen Firewall | Application-aware threat detection | Needs regular tuning and updates | Environments needing deep traffic visibility |
Connectivity Infrastructure Considerations
Different connectivity solutions like fiber, satellite, and hybrid networks create different security requirements. Fiber provides dedicated bandwidth and naturally isolates your traffic from neighbors. Wireless and public internet connections require heavier encryption and verification layers. A healthcare clinic in a rural area might combine satellite connectivity for redundancy with cellular backup, each requiring different security approaches. Your connectivity infrastructure choice shapes which secure solutions work best.
Pro tip: Map your current connectivity infrastructure and honestly identify where data stops being encrypted or where user verification drops off. Many breaches happen not because security technology failed, but because a specific connection type between systems never received security controls in the first place.
How Secure Connectivity Supports Daily Operations
Secure connectivity is not something that happens in the background while your organization operates. It is the foundation that makes your operations possible. When a healthcare clinic schedules patient appointments, pulls medical histories, processes insurance claims, and coordinates with specialists across multiple locations, every single one of those actions depends on secure connectivity working perfectly. When a retail chain manages inventory across 50 stores, coordinates staffing, processes transactions, and handles customer data, disruptions to secure connectivity don’t just slow things down. They stop revenue. They create compliance violations. They put customer trust at risk.
Consider what happens during a normal shift at a mid-sized healthcare facility. Building automation systems regulate temperature and humidity in operating rooms and sterile storage areas. HVAC systems keep air quality within clinical specifications. Alarm systems alert staff to patient emergencies. Security systems control access to pharmacy and records storage. Lighting systems adjust based on time and occupancy. All of these systems are operational technology that must remain available and functional. When secure connectivity principles for operational technology are implemented correctly, these systems continue operating reliably while remaining protected from unauthorized access. But here is the hard truth: many healthcare facilities still operate with building automation, HVAC controls, and alarm systems that use old protocols with minimal security. A breach that compromises one of these systems could disrupt patient care or create safety hazards.

Retail operations face similar complexity. Point-of-sale systems process transactions and collect payment data. Inventory management systems track merchandise across locations. Security cameras and alarm systems protect against theft and create liability documentation. Customer Wi-Fi networks provide convenience while creating potential entry points for attackers. Time clock systems track employee hours. Supply chain management systems coordinate with vendors and logistics providers. When secure connectivity connects all these systems while maintaining proper segmentation and access controls, your organization can operate at full efficiency. Individual systems can do their jobs. Data flows where it needs to go. Authorized people can access what they need. Unauthorized access gets stopped before it creates problems. But when secure connectivity is weak or incomplete, you get complexity without safety. You get efficiency without visibility. You get systems talking to each other in ways you don’t actually understand.
Real-time analytics and monitoring become possible with secure connectivity. Your healthcare organization can track patient outcomes across locations and identify trends. Your retail operation can see sales patterns, customer traffic, and inventory movement in real time. Predictive maintenance becomes feasible when your systems can securely communicate device health data without exposing critical infrastructure to the internet. Secure connectivity for operational technology in healthcare settings ensures that this data flows continuously while maintaining manual override capabilities. If your secure connectivity fails, your systems can still function independently. Your backup generators still work. Your emergency lighting still illuminates. Your critical systems can operate manually if necessary. This is not just a technology feature. It is a continuity requirement.
The relationship between secure connectivity and operations reveals something important: you cannot bolt security onto operations as an afterthought. When a clinic adds secure connectivity thoughtfully during infrastructure planning, they build systems that are secure by design. When a retail chain retrofits security into existing connectivity, they often create gaps and workarounds that undermine the security. Your operational technology teams need to collaborate directly with your security teams from the start of any infrastructure project. Your HVAC technician needs to understand why certain ports are blocked. Your inventory manager needs to know why certain devices cannot access certain servers. Your staff needs to understand the manual procedures that work when secure connectivity systems fail. This collaboration prevents the scenario where everyone blames someone else when a secure connectivity failure creates operational problems.
Remote administration capabilities illustrate the operational benefit of secure connectivity. When your retail district manager needs to review store-level inventory or your healthcare administrator needs to check patient census across locations, secure connectivity enables that access. But secure connectivity requires that remote access goes through verified channels using strong authentication. It does not mean anyone with internet access can reach any system. It means authorized people can perform their jobs remotely while unauthorized access gets blocked automatically.
Pro tip: Before implementing new operational systems or expanding existing ones, create a connectivity matrix listing every system, what data it accesses, who needs access to it, and what connectivity it requires. Share this matrix with both your operations teams and security teams. Disagreements about this matrix will reveal where secure connectivity planning is incomplete.
Regulatory Impact for Healthcare and Retail
Regulatory frameworks are not suggestions for healthcare and retail organizations. They are legal requirements backed by significant penalties, and they increasingly mandate specific secure connectivity standards. Your secure connectivity strategy is not actually optional. It is a compliance requirement shaped by regulations that your industry regulators and your legal team take very seriously. Understanding what these regulations require helps you build connectivity infrastructure that satisfies compliance demands while actually protecting your organization.
Healthcare organizations operate under HIPAA, which requires that protected health information be encrypted both in transit and at rest. The Security Rule specifies that access controls, audit logging, and encryption must be in place. It does not just recommend these controls. It requires them as a condition of operating legally. HIPAA violations result in fines ranging from $100 to $50,000 per record exposed, and a single breach affecting thousands of patient records generates catastrophic financial penalties. Beyond the financial impact, HIPAA violations trigger mandatory breach notification, damage your reputation with patients, and create liability exposure if patients experience harm from the breach. Healthcare cybersecurity challenges including ransomware attacks are forcing healthcare organizations to adopt secure connectivity frameworks specifically designed to meet these regulatory requirements while protecting against evolving threats.
Retail organizations face similar mandatory requirements under PCI DSS (Payment Card Industry Data Security Standard). If your retail store processes, stores, or transmits credit card data, you must comply with PCI DSS regardless of your organization size. PCI DSS requires network segmentation so credit card data never touches systems processing other functions. It mandates encryption for cardholder data. It requires strong access controls and continuous monitoring. It specifies that you must maintain a firewall configuration and update it regularly. Non-compliance with PCI DSS exposes your organization to fines from payment card processors, potential loss of ability to accept credit cards, and liability if customer payment data gets breached. Additionally, state-level regulations increasingly require notification of breaches and specific data protection standards. A retail operation in New York must meet New York’s data protection requirements. A retailer in California must meet California’s requirements. These regulations are increasingly converging on secure connectivity as a baseline requirement.
Beyond HIPAA and PCI DSS, additional regulations shape secure connectivity requirements. State data breach notification laws require notification within specific timeframes if personal information is compromised. Healthcare organizations must meet state-specific privacy laws that sometimes exceed HIPAA requirements. Retail organizations must comply with regulations covering consumer privacy, employment records, and financial data. Global regulatory best practices and policies are increasingly emphasizing harmonized standards for data protection and operational resilience, meaning that secure connectivity requirements are becoming more consistent across jurisdictions even as specific regulations evolve. Your Mid-Atlantic location means you navigate multiple regulatory environments. A healthcare system operating in Maryland, Pennsylvania, and Virginia faces slightly different regulatory interpretations in each state. A retail chain with locations across multiple states must maintain connectivity and security standards that satisfy the most stringent requirements across all locations.
The Business Case Beyond Compliance
Compliance with regulations matters, but here is the reality: organizations that frame secure connectivity purely as a compliance requirement often get the implementation wrong. They build just enough connectivity security to satisfy auditors and then stop. They create security theater rather than actual security. Smart CIOs use regulatory requirements as the floor, not the ceiling. Regulations require encryption. Smart organizations implement encryption plus real-time threat monitoring. Regulations require access controls. Smart organizations implement access controls plus behavioral analytics to detect when authorized users access data in unusual ways. Regulations require breach notification procedures. Smart organizations design systems to prevent breaches in the first place.
The business case for secure connectivity extends beyond regulatory compliance. Healthcare organizations that maintain strong secure connectivity experience fewer ransomware attacks, which means less downtime and lower costs from productivity losses. Retail organizations with robust secure connectivity suffer fewer credit card breaches, which means lower fraud losses and lower processing fees. Both types of organizations that implement secure connectivity thoughtfully maintain customer trust, which drives patient retention and customer loyalty. A single publicized breach damages reputation in ways that cost far more than the fines.
Pro tip: Schedule a meeting with your compliance officer and your security team specifically to review which regulations apply to your organization and what secure connectivity requirements each regulation imposes. Create a matrix matching regulatory requirements to specific technical controls you have implemented. Gaps in this matrix are not compliance risks. They are business risks.
Risks of Poor Connectivity and Mitigation Strategies
Poor connectivity creates cascading problems that ripple through your organization in ways that are not always obvious until they manifest as major incidents. A healthcare clinic with unreliable secure connectivity experiences dropped patient records, missed appointment notifications, and delayed test results. A retail operation with weak connectivity loses transaction data, cannot sync inventory accurately, and creates friction for customers at checkout. But the real danger goes deeper. Poor connectivity creates security vulnerabilities because organizations trying to maintain operations despite connectivity problems often implement workarounds that bypass security controls. Your staff creates local copies of sensitive data to work offline. Your locations install unauthorized internet connections when the primary link fails. Your systems fall back to unencrypted communication when encrypted channels become too slow. Every workaround weakens your security posture.
Unauthorized access represents one of the most immediate risks associated with poor connectivity. When your secure connectivity infrastructure fails or performs poorly, attackers exploit the gap. Weak or missing encryption creates opportunities for data interception. Poor access controls mean unauthorized devices or users can connect to networks. IoT devices and operational technology systems connected through poor connectivity become entry points for attackers who use lateral movement through unsecured networks to move from compromised devices into your critical systems. In healthcare, this could mean attackers accessing patient data from a compromised printer. In retail, attackers might compromise a point-of-sale system and use it to reach your payment processing backend. Once inside, they move laterally through your network because poor connectivity infrastructure lacks the segmentation and monitoring that would detect and stop this movement.
Operational disruption becomes another critical risk. Healthcare organizations experiencing poor connectivity cannot reliably access Electronic Health Records, which directly impacts patient safety. Clinicians make decisions based on incomplete information or stale data. Pharmacy staff cannot verify medication histories. Lab systems cannot reliably transmit results. Retail organizations with poor connectivity cannot process transactions reliably, which means lost sales and frustrated customers. Supply chain systems fail to update inventory, creating stockouts and overstock situations. Your organization continues technically operating but at degraded capacity. Revenue suffers. Customer satisfaction declines. Employee frustration increases. These operational impacts sometimes exceed the financial damage from security breaches.
Mitigation Strategies That Actually Work
Mitigation starts with recognizing that connectivity and security must be engineered together from the beginning, not bolted together afterward. A defense-in-depth approach means multiple layers of protection that work together. You cannot rely on a single firewall or a single encryption protocol. Instead, you implement redundant systems that protect each other. Your primary connectivity path uses strong encryption and authentication. Your backup path uses the same security standards. Your monitoring systems track both paths continuously. If one path gets compromised, the backup path remains secure. If one monitoring system fails, the other continues watching.
Redundancy serves as a critical mitigation strategy. Single points of failure kill organizations. Your healthcare clinic needs backup internet connectivity so if your primary provider has an outage, you can switch to backup automatically. Your retail locations need multiple ways to reach your central systems. Your connectivity architecture should include multiple internet service providers, diverse network paths, and automated failover so that poor performance or failure on one path automatically switches traffic to another path without manual intervention. This redundancy adds cost upfront but prevents catastrophic losses when connectivity fails.
Monitoring and recovery capabilities complete the mitigation picture. You cannot mitigate what you cannot see. Real-time monitoring of your connectivity infrastructure reveals problems before they impact operations. You track latency, packet loss, error rates, and security events continuously. You establish alert thresholds so your team gets notified when connectivity degrades below acceptable levels. You define recovery procedures so your team knows exactly what steps to take when problems occur. You test these procedures regularly so staff can execute them quickly when needed.
Infrastructure investment in reliable business connectivity combined with regulatory policies that emphasize security and resilience creates the foundation for strong mitigation. Organizations cannot build secure connectivity on inadequate infrastructure. If your primary connectivity cannot handle your organization’s traffic load, poor performance becomes inevitable. Your security controls then degrade as people find workarounds. Investing in adequate bandwidth, modern equipment, and redundant systems prevents this degradation.
Pro tip: Conduct a connectivity failure scenario exercise where you walk through what happens if your primary internet connection fails for 24 hours. Can your operations continue? What data becomes inaccessible? What manual processes can your team activate? This exercise reveals gaps in your redundancy and recovery planning before failure actually occurs.
Comparisons With Traditional, Less-Secure Networks
Most organizations did not start with secure connectivity. They started with basic connectivity and bolted security on top later. This approach created networks that technically function but remain fundamentally vulnerable. Understanding how traditional, less-secure networks differ from modern secure connectivity architectures helps explain why your organization cannot simply keep doing what you have always done and expect different security outcomes. The differences are not subtle. They are architectural and fundamental.
Traditional wireless networks rely on older security protocols that have known vulnerabilities. WEP (Wired Equivalent Privacy), for example, was the standard for wireless security in the early 2000s. It used weak encryption with key reuse issues that allowed attackers to crack encryption keys in minutes with basic tools. WPA represented an improvement, but many implementations still exist in healthcare clinics and retail locations because replacement felt expensive. Modern wireless security protocols implement stronger encryption with better authentication mechanisms and integrity checks, making brute force attacks impractical. The difference is not incremental. A network running WEP in 2024 has essentially zero protection against modern attackers. A network running modern WPA3 with proper configuration creates security challenges that require sophisticated attacks to overcome.
Traditional network architectures were designed when most traffic stayed inside organizational boundaries. You had a headquarters. You had branch offices. Traffic moved through dedicated leased lines you controlled. Security meant controlling who could access your physical network. This model creates visibility problems because static network configurations are hard to manage and harder to change quickly. When your healthcare clinic wants to add a new medical device or your retail location needs to add a new POS system, traditional networks often require manual configuration by IT staff. This creates delays, creates opportunities for misconfiguration, and creates security gaps. Traditional IP networks are harder to manage and more prone to configuration errors compared to modern software-defined approaches. A single misconfigured router in a traditional network might expose sensitive data to the entire internet. Finding that misconfiguration requires manual inspection of dozens of configuration files across multiple devices.
How Modern Secure Connectivity Differs
Modern secure connectivity architectures use software-defined approaches that centralize control and create consistency across your entire infrastructure. Instead of configuring each device individually, you define security policies once and apply them consistently everywhere. Your rules for how patient data moves, who can access inventory systems, and which devices connect to your network are defined in one place. Every device in your infrastructure automatically enforces those rules. When you discover a new threat, you update your security policies in one place and the change applies automatically across your entire organization. Traditional networks require manual updates to each device, which means updates might happen at different times, creating windows where some devices are protected while others are not.
Visibility reveals another fundamental difference. Traditional networks often have blind spots because traffic passes through devices that do not have sophisticated inspection capabilities. A traditional firewall sees traffic entering and leaving your network but may not see traffic moving between internal systems. A compromised device on your network talking to another device on your network often happens invisibly to your security team. Modern secure connectivity architectures provide continuous visibility into traffic patterns, allowing you to detect when authorized users access data in unusual ways or when compromised devices attempt lateral movement. This visibility enables detection and response before attackers cause serious damage.
Authentication mechanisms have evolved dramatically. Traditional networks often authenticate users once at login and then trust them for the entire session. Modern secure connectivity implements continuous authentication, verifying not just who users are but also whether their devices remain trustworthy, whether they are accessing data from expected locations, and whether their access patterns match normal behavior. A user accessing patient records from their expected office location during business hours gets different access scrutiny than the same user accessing records from a international IP address at 3 AM.
Redundancy and recovery have become architectural expectations rather than afterthoughts. Traditional networks often have single points of failure because backup systems were expensive. Modern secure connectivity assumes redundancy as a requirement. Multiple internet service providers, geographically diverse data centers, and automated failover systems ensure that failures in one component do not take down your entire infrastructure. This resilience costs less than recovering from a major outage.
This summary highlights key differences between traditional and modern network security approaches:
| Attribute | Traditional Networks | Modern Secure Connectivity |
|---|---|---|
| Control | Device-by-device, manual | Centralized, automated enforcement |
| Visibility | Limited internal monitoring | Continuous real-time insights |
| Recovery | Single points of failure | Built-in redundancy and failover |
| Authentication | Initial login only | Ongoing user/device verification |
| Compliance Support | Harder to document, inconsistent | Aligned with industry regulations |
Pro tip: Ask your infrastructure team which wireless security protocol your organization currently uses and when it was deployed. If the answer is WPA or older, upgrading to WPA3 should become an urgent priority because the security vulnerability is not theoretical. It is real and exploitable by anyone with basic technical skills.
Strengthen Your Secure Connectivity with SabertoothPro Solutions
Managing secure connectivity means facing challenges like continuous device verification and real-time data protection that the article highlights. Your critical goal is to close gaps in encryption, access control, and network visibility to protect sensitive information and comply with regulations. SabertoothPro understands these pain points and offers tailored solutions like our Titan WiFi Hotspot Plans designed for reliable and encrypted wireless connectivity that keeps your operations running smoothly with minimal vulnerabilities.
Take control of your network security now with SabertoothPro’s high-speed internet and enterprise IT services. From next-gen firewalls and zero-trust frameworks to flexible IoT integration and secure Wi-Fi extenders, we provide the infrastructure you need for seamless and compliant connectivity. Visit https://sabertoothpro.com to explore how our solutions can protect your healthcare or retail environment today. Don’t wait until a breach disrupts your operations. Connect securely and confidently today.
Frequently Asked Questions
What is secure connectivity?
Secure connectivity refers to network communications that are protected through encryption, authentication, and continuous monitoring to prevent unauthorized access and data breaches.
Why is secure connectivity important for CIOs?
Secure connectivity is crucial for CIOs as it protects sensitive data such as patient records and payment information, ensuring compliance with regulations and safeguarding against cyber threats.
How do common myths about cybersecurity affect secure connectivity?
Common myths, such as believing small networks don’t attract attackers or that firewalls provide all the security needed, can lead CIOs to overlook critical components of a secure connectivity strategy, resulting in vulnerabilities.
What types of secure connectivity solutions are available?
Several secure connectivity solutions include Virtual Private Networks (VPNs), Zero-Trust Architecture, Software-Defined WAN (SD-WAN), Network Segmentation, and Next-Generation Firewalls (NGFWs), each offering different strengths and weaknesses for protecting networks.


